Insecure Docker Registries and RHEL7

Insecure registry Pushing from Docker. Let’s assume the private insecure registry is at 10.141.241.175 on port 32000. The images we build need to be tagged with the.
In developing and deploying Docker applications it is sometimes necessary to push and pull images to/from a HTTP Docker registry. This is considered very insecure and HTTPS is preferred, but when you don’t control the registry yourself you may need to resort to this option. This guide describes how to push/pull images to/from a plain HTTP Docker registry from Red Hat Enterprise Linux 7.2, where the exact steps are non-obvious.

Docker Insecure Registry Tutorial
The official Docker documentation says to add the --insecure-registry flag to your docker engine’s configuration file and restart the daemon but doesn’t give the precise commands for RHEL7, so here they are.
That’s it. Now go secure that Docker registry!

Docker Insecure Registry Settings
- In order to do this in the context of the docker-in-docker service, one must pass this configuration to the service. This can be done by updating your gitlab-ci.yaml to specify the service as: services: - name: docker:dind command: '-insecure-registry=myregistry.gitlab.com' Share. Improve this answer. Answered May 2 '18 at 11:02.
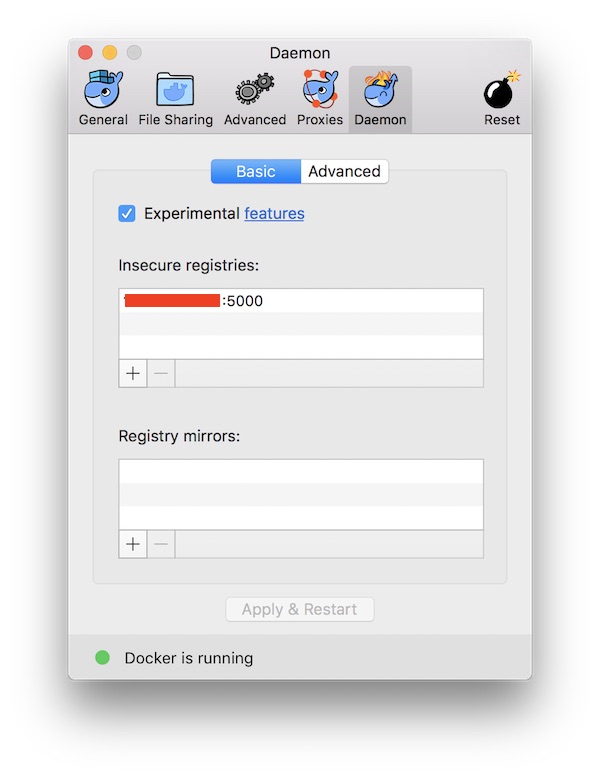
- Then open the Daemon tab and enter registry.local:5000 in the insecure registries list-you can see my settings in figure 5.6. Figure 5.6 Allowing an insecure registry to be used in Docker Desktop. The Docker Engine needs to be restarted to load any new configuration settings, and Docker Desktop does that for you when you apply changes.
Comments are closed.